Security Alerts
Scammers Are Taking Advantage of Fears Surrounding the Coronavirus. Remember To Always Keep Your Sensitive Info Safe.
Honor Bank will never call, email or contact you to request your online credentials or debit PIN information, including:
- User ID
- Password
- Other login credentials
- Call us immediately at 877-325-8031 if you receive any calls requesting your information, even if the call appears to be coming from Honor Bank as this is a common spoofing method. Hang up and call us directly.

MORE WAYS TO KEEP YOUR INFORMATION SAFE:
- Shop on secure websites – Look for “https” in the web address.
- Don’t use public Wi-Fi to shop – It’s not secure.
- Watch out for scams – If someone contacts you asking for money to help a loved one, contact the person in need directly. Never give your user IDs or passwords to anyone over the phone or email.
- Don’t trust email – Don’t click links in emails unless you know where they go, or type in the link directly. Don’t open attachments from email addresses you don’t know
- Vary and change passwords and user IDs – Keep them complicated using a variety of numbers, letters and characters
- Track your transactions – Use online & mobile banking, If you didn’t make a purchase contact Honor Bank immediately.
- Beware of e-skimmers on ATMs and debit card readers – Investigate the card reader to make sure nothing looks or feels unusual. If something doesn’t seem right report your concerns.
March 2020
Google recently removed several applications (apps) from their Google Play store because they contained a strain of “clicker” malware that can view your sensitive data and even make in-app purchases on your behalf. Even though they have now removed these apps there could still be more they don’t know about.
This is not the first time that applications with “clicker” malware have been removed from official Android and Apple app stores, and it will not be the last. Ensuring the security of mobile applications is an ongoing challenge.
Consider the following before downloading any application:
- Do your research: Read app reviews, but make sure they’re not fake or staged! Be wary of applications that don’t have any reviews.
- Avoid applications that have a low number of downloads.
- Look for strange context or spelling errors in the application’s description.
- Consider investing in cybersecurity protection for your mobile device.
When in doubt, avoid downloading questionable applications, and look for a safer alternative.
February 2020
The Department of Homeland Security warns that desktop (and laptop) versions of the Firefox web browser are under active, targeted attacks that allow hackers to take control of an entire operating system – whether it is Windows or Mac.
To upgrade your Firefox browser:
- On a Mac: launch Firefox and click About > Firefox
- Click the “Restart to update Firefox” button
- On a PC: launch Firefox and go under Options > Firefox Updates or Options > Advanced > Update
To be protected from this vulnerability, you want to be running Firefox 72.0.1 and Firefox ESR 68.4.1 or higher. Firefox browsers on mobile devices are not known to be affected.
January 2019
The holiday season has come and gone, but the bad guys are here to stay. Scammers are still using holiday shopping deals to lure you in. They’re posing as popular retailers and sending dangerous emails and text messages that tell you to claim the reward points that you’ve supposedly earned with your holiday purchases.
The bad guys use logos and company colors to make the emails and text messages look legitimate. Don’t fall for it! If you click the phishing links in these emails or text messages, you are actually downloading malware to your computer or phone. This malware allows the criminals to gain access to your device; therefore, leaving your personal information at risk.
Always remember: Never click on a link that you weren’t expecting. If you receive an email from a retailer or service that you use, log in to your account through your browser (not through links in the email) to make sure it’s valid.
November 2019
Since most people are familiar with the popular streaming service, the bad guys often use Netflix as bait in phishing attacks. One recent Netflix scam starts with an email claiming that you’ve missed a payment and that your subscription has ended. You’re instructed to use the links in the email to log in to your account and fix your billing information.
The emails in this particular phishing campaign usually include misspellings and improper grammar. But if you fail to notice these clues and proceed to click the link in the email, you’re brought to a fake login page. The login page looks legitimate and so does the page where you’re told to enter your payment card details.
Don’t fall for it! Remember the following to help stay safe online:
- Never click on links in an email you weren’t expecting.
- When you receive an email asking you to log in to an account or online service that you use, log in to your account through your browser–not through links in the email. This way, you can ensure you’re logging into the real website.
- Be wary of emails with spelling or grammar errors, especially when it supposedly came from a reputable source.
October 2019
The bad guys are at it again. They’re posing as well-known services–such as Gmail, Amazon, and Paypal–so they can bait you into giving up your personal and financial information.
The phishing attack starts off with a common tactic: You receive an email claiming that you need to verify your account. The scammers send their emails from an active domain, which makes it look more legitimate and makes it easier for them to bypass email security filters. Once you click the button or link in the email, you’re stepped through several stages of the attack. You’re first brought to a website that is only used to redirect you to a second page. This helps the hackers get past email filters. From the second page, you’re asked to verify that you’re not a robot. Once this fake site has confirmed you’re not a robot, the real danger begins. On the final phishing page, you’re asked to fill in fields with your account credentials, credit card details, and other sensitive information. Nothing happens when you click the button to submit your information, but all of your data has already been sent directly to the attacker’s email address.
Always remember: If you receive a suspicious email from an online service that you use, log in to your account through your browser (not through links in the email) to check the validity of the information. Even if the sender’s email address appears to be from a well-known organization, the email address could be spoofed.
September 2019
The bad guys are targeting Amazon customers and tricking them into giving up their account login details, personal information, and even their financial information. They’re sending phishing emails that tell you to update your account information within twenty-four hours or your account will be permanently disabled. Don’t fall for this warning! Cybercriminals are counting on your impulsive reaction.
Once you click the “Update Now” button in the phishing email, you’re taken to a realistic-looking Amazon login page. After you’ve entered your credentials, another form is displayed for you to “update” your name, phone number, date of birth, and address. Then, you have to provide your credit card and bank account details.
After you’ve given up all of this sensitive data, the phishing site tells you your account has been recovered and that you’ll be logged out automatically. You’re then redirected to the real Amazon website without having any idea of what actually happened.
Always remember: If you receive a suspicious email from an online service that you use, log in to your account through your browser (not through links in the email) to check the validity of the information presented. Also, be careful with emails that are seemingly urgent. The bad guys often use a ‘sense of urgency’ to pressure you into clicking as an impulsive response.
August 2019
Beware! If you use Gmail for your business or personal email, you could be at risk. One of the latest cyber scams going around takes advantage of the popular Google Calendar service by adding fake events to unsuspecting victims’ calendars.
When they create the calendar event, they add a short event description complete with a dangerous phishing link. Typically, the event claims that “You’ve won prize money”, or that “There’s a money transfer in your name”. The description tells you to click the link and follow the directions to claim your money.
Once invited, you’re exposed to the dangerous event description in multiple ways: You’ll receive a notification in your inbox and the event will automatically show up on your calendar. Don’t fall for it! If you click the link in the event description, you’re brought to a dangerous webpage and instructed to enter your personal information so the bad guys can steal it.
Remember the following to avoid falling for scams like this:
- Never click on links in emails or in calendar notifications that you weren’t expecting. Even if it appears to be from someone you know, it’s best to pick up the phone and call them to be sure it’s legitimate.
- Always hover over links to see where they’re taking you before clicking. The link may take you to a different address from the URL that is shown.
- By default, Google Calendar events are automatically added to your calendar, even if you haven’t responded. You can turn this setting off by opening your Google Calendar settings from a desktop browser.
July 2019
The bad guys have crafted emails that spoof Office 365 and warn that your files are being “deleted”. They’re sending these emails to a great majority of Office 365 users.
If you click any links in the email you’re brought to a realistic-looking Office 365 login page, but the page is certainly not from Microsoft. If you enter your credentials here they’ll be stolen and sold to other criminals, or used to perform more complex attacks on your organization.
Remember, always hover over links to see where they’re taking you before clicking. Never click on links unless you’re certain the sender is legitimate. Whenever you get an email from an online service you use, log in to your account through your browser. Never click links in emails if you’re not sure whether the message is valid.
June 2019
According to recent reports, phishing attacks that use brand impersonation are at an all-time high. Cyber criminals are posing as familiar companies so they can trick you and get access to your account in order to steal sensitive data or target additional employees.
Here’s how it typically happens: Attackers send you a standard-looking email appearing to be from a service or company that you use, such as Office 365. Clicking the link in the email will take you to a fake (but very realistic) login page. The most deceiving part of some of these fake pages is that the web address appears to be safe. The URL may end with a legitimate domain like “windows.net”, because the bad guys are hosting these pages with Microsoft’s Azure cloud services. If you enter your information here, the bad guys will gain access to one or more of your accounts which they can use to steal data or plan further attacks on your organization.
Remember the following to protect yourself from your inbox:
- Look out for strange or suspicious domains in sender addresses. Even if the domain looks legitimate, check again. Does the email say “micronsoft.com” instead of “microsoft.com”
- Before clicking, always hover over links to see where they are taking you. Never click on a link in a message unless you’re certain the sender is legitimate.
- Whenever you get an email from an online service you use, log in to your account through your browser (not through links in the email) to check whether the email message is valid.
April 2019
PDF files are commonly used in most organizations, regardless of what industry you work in. That’s why PDFs are often thought of as a “safe” file type. Do you hesitate to open them?
Over the past few months, there’s been an increase in the bad guys taking advantage of this trusted file type. They’re finding ways to hide malware in PDFs so they make it past the security filters your organization has in place. Most often, the malware is executed once you open the PDF and click on a misleading link in the file. A different PDF attack steals your login details when you open the file.
Always remember, never open an attachment unless you have asked for it. Even if the attachment appears to come from someone you know, pick up the phone to verify it’s legitimate.
March 2019
The bad guys are automating robocall scams worldwide. Recently, there has been a rise in this type of fraud. They have a variety of attacks that you should watch out for. Here are a few examples:
- Bank account and credit card scams where the bad guy claims to be an official from your bank or card company
- Extortion scams where they request payment for a kidnapped friend or family member
- Callback Scams where you are tricked into calling back a very expensive international number
Remember the following to avoid robocall scams:
- If you receive a call from a company urging you to complete a request, hang up and call back the company directly to investigate.
- Scammers can spoof any number they’d like. Therefore, even if a call looks like its coming from a familiar source, it could be a scam.
- Never provide personal information over the phone unless you’re the one who initiated the call.
Think Before You Pick Up!
January 2019
The bad guys are back to their old tricks with Netflix again. They are sending out email messages asking users to update their billing information but don’t click that link! If you do, the bad guys could steal your login details, your credit card data, your picture, your ID, and even more if they gain access to your computer or network.
Here are some tips on how to stay safe:
- Never click on a login link or an account verification link in an email.
- Check for the green HTTPS padlock in your browser’s address bar. If there isn’t one, it means the site is not secure.
- If there is a green HTTPS padlock in your browser’s address bar, check the web address of the site. If it’s not exactly what you expect, don’t click!
- Don’t ignore telltale signs that it’s a scam such as spelling and grammar errors.
- Guard your ID closely. Never give away a picture of yourself or your ID when it isn’t absolutely necessary.
December 2018
Stay cyber-secure this holiday season. Below are the 12 Scams of Christmas to keep your eyes out for. Learn more.
October 2018
The bad guys are getting creative with a new hybrid attack that involves CEO Fraud and gift card scams.
There is a massive campaign underway where they impersonate an executive and urgently ask for gift cards to be bought for customers. Once the gift cards are physically bought from a store, the “boss” asks you to send them the redeem code/number via email or text.
Never comply with a request like this – it’s a scam! Always confirm a request with your boss over a live phone call or in person to make sure it’s not a scam. Sometimes it’s OK to say “no” to the boss!
September 2018
The bad guys know you like free stuff, but this time it’s going to cost you! They lure you to a fake website for a “free” gift card in exchange for seemingly harmless information. Once on the site, you are asked a series of questions. If you make it through all of the questions, you’ll earn a unique code to redeem a gift card – this code and gift card are worthless!
The bad guys are tricking you into offering up your personal information. Don’t be the victim!
Never share your sensitive data and always check if an offer is legitimate by contacting the company making the offer. Remember, there’s no such thing as a free lunch.
August 2018
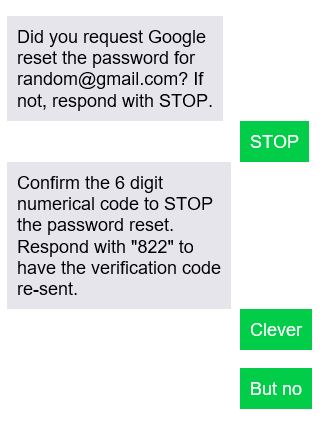
There is a new scam where hackers send you a text that asks you about a password reset on your account. If you did not request a password reset, they tell you to respond with STOP. This is a scam. The bad guys asked for that password reset and now want you to send them the authorization code! Don’t fall for it. Below is an example of how the scam works:
Remember, Gmail will never ask for confirmation to NOT make changes to your account. You didn’t ask for a password reset, so you shouldn’t be asked about one. Do not reply to the text (doing so will tell the scammers that they have reached a valid number). To prevent losing your account to bad guys, it’s a very good idea to have 2-step verification set up on your Google account. For more information about Google 2-step verification, copy and paste the link below in to your browser: https://www.google.com/landing/2step/
July 2018
The bad guys love to spoof companies that we’re all familiar with. If you’re an Apple customer, you know they send emails on a regular basis, and this might make you inherently less suspicious of anything appearing to come from Apple.
Lately there’s been an increase in “Apple” scams. One of these phishing scams appears as a fake email invoice for your “recent Apple purchase”. Another scam is a “Reminder” email notifying you of an account login from an iPad in Monaco. The third, and possibly most attention-grabbing scam, is a smishing attempt informing you (via text message) that your Apple ID is expiring today. Any Apple user knows how vital an Apple ID is, and these hackers are purely relying on shock factor to hook their victims.
Always Remember: If you get a suspicious email or text from an account or online service that you use, log into your account through your browser (not through links in the email) to check the validity of the information presented in the suspicious email.
June 2018
There is a new Direct Deposit phishing attack you need to watch out for. It’s a sophisticated scam that starts with an official-looking email that asks you to click a link and access a website. Next, they ask you to confirm the data with your real username and password. Last, they use your info to access payroll portals, and reroute your direct deposit amounts to bank accounts owned by the bad guys. The lesson here is to never give anyone your credentials in response to an email.
September 2017
If you have a credit report, there’s a good chance that you’re one of the 143 million American consumers whose sensitive personal information was exposed in a data breach at Equifax, one of the nation’s three major credit reporting agencies.
Here are the facts, according to Equifax. The breach lasted from mid-May through July. The hackers accessed people’s names, Social Security numbers, birth dates, addresses and, in some instances, driver’s license numbers. They also stole credit card numbers for about 209,000 people and dispute documents with personal identifying information for about 182,000 people. And they grabbed personal information of people in the UK and Canada too.
There are steps to take to help protect your information from being misused. Visit Equifax’s website, www.equifaxsecurity2017.com.
- Find out if your information was exposed. Click on the “Potential Impact” tab and enter your last name and the last six digits of your Social Security number. Your Social Security number is sensitive information, so make sure you’re on a secure computer and an encrypted network connection any time you enter it. The site will tell you if you’ve been affected by this breach.
- You also can access frequently asked questions at the site.
HERE ARE SOME OTHER STEPS TO TAKE TO HELP PROTECT YOURSELF AFTER A DATA BREACH:
- Check your credit reports from Equifax, Experian, and TransUnion — for free — by visiting annualcreditreport.com. Accounts or activity that you don’t recognize could indicate identity theft. Visit IdentityTheft.gov to find out what to do.
- Consider placing a credit freeze on your files. A credit freeze makes it harder for someone to open a new account in your name. Keep in mind that a credit freeze won’t prevent a thief from making charges to your existing accounts.
- Monitor your existing credit card and bank accounts closely for charges you don’t recognize.
- If you decide against a credit freeze, consider placing a fraud alert on your files. A fraud alert warns creditors that you may be an identity theft victim and that they should verify that anyone seeking credit in your name really is you.
- File your taxes early — as soon as you have the tax information you need, before a scammer can. Tax identity theft happens when someone uses your Social Security number to get a tax refund or a job. Respond right away to letters from the IRS.
- Visit Identitytheft.gov/databreach to learn more about protecting yourself after a data breach.
Have questions? We’re here to help. Contact us.
June 2017
You may have already heard in the news about another widespread ransomware attack taking down large companies, hospitals, and transportation systems around Europe and the U.S. Labeled “NotPetya” by security authority Kaspersky Lab, it uses the same Windows vulnerability that the “Wannacry” ransomware did just a few weeks ago.
How does NotPetya work?
NotPetya doesn’t just encrypt files, it also overwrites the Master Boot Record. This renders the machine unusable and prevents users from recovering any information on it. Unlike WannaCry, Petya does not include any type of “kill switch”
If you have been infected
- Do not pay. You will not only be a financial criminal, but you are also unlikely to regain access to your files. The email account used to manage ransom demands, in this case, has been blocked. So the attackers’ only known channel for communication at the moment, has been rendered useless.
- Make sure that you keep a copy of the phishing email received from the attackers and provide it with the police, as it helps with their investigation.
- Disconnect infected devices from the internet. If the infected device is part of a network, isolate it as soon as possible, to prevent the spread of the virus to other nodes in the network.
- You can then format the hard drive, reinstall the operating system and apps, run any available updates and, finally, restore the locked files from your backup device
If you have not been infected
- Keep all applications and the Operating System up to date. If you are offered the option of automatic updates by your device, take it.
- Keep your data backed up, and create two copies – one in the cloud, and one is physical storage. It is easy to retrieve those files even if you are affected by Ransomware. Use robust security products to protect your system from all threats, including ransomware.
- Do not use high privileges accounts (accounts with administrator rights) for daily business.
- Even if trusted parties like banks send you suspicious or unexpected emails, do not click on the attachments or the links.
May 2017
The ransomware attack, known as “Wannacry,” has affected over 200,000 individuals and organizations worldwide, with a vast majority in Europe and Asia. As of the writing of this communication, there have been no infections detected or reported at any of Safety Net’s client sites. We proactively ran full scans on various systems to be certain.
The cyber-attack that began on Friday, May 12, took advantage of a vulnerability in the Windows Operating System (OS). Safety Net had already pushed out a Microsoft patch that addressed the vulnerability during regular maintenance windows. Symantec created and pushed out a fix for the worm, as well.
This outbreak is a good example of why diligent maintenance of multi-layered protection (antivirus, patches, spam filtering, firewalls, and user education) is so important.
May 2017
Google Docs users were recently hit with a phishing scam. During the attack, users were sent a deceptive invitation to edit a Google Doc, with a subject line stating a contact “has shared a document on Google Docs with you”.
The email address hhhhhhhhhhhhhhhh|@|mailinator[.]com was also copied in to the message; Mailinator, a free email service provider has denied any involvement.
If users clicked on the “Open in Docs” button in the email, they were then taken to a real Google-hosted page and asked to allow a seemingly real service, called “Google Docs”, to access their email account data.
By granting permission, users unwittingly allowed hackers to potentially access to their email account, contacts and online documents. The malware then e-mailed everyone in the victim’s contacts list in order to spread itself.